How can Businesses Combat Advanced Persistent Threat?
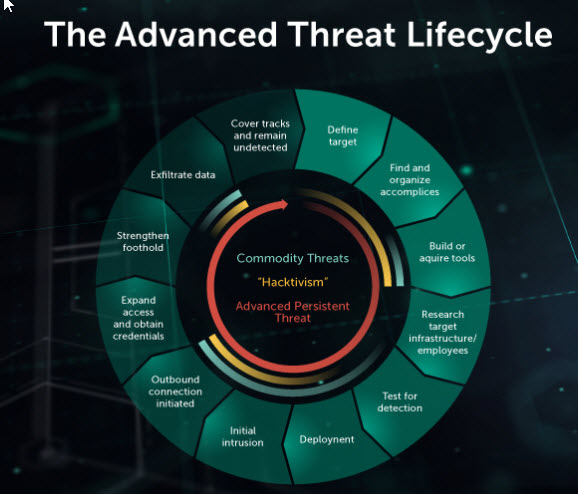
An advanced persistent threat (APT) is a broad category for an attack initiative. An attacker, or a group of trespassers, demonstrates a long-term illicit existence on a system to extract highly sensitive information.
The aims of these attacks, which are carefully selected and studied, are usually large corporations or government systems. The ramifications of such invasions are many and include:
- Theft of intellectual property (e.g., trade secrets or patents)
- Sensitive data has been exposed (e.g., employee and user private data)
- Critical organizational assets are being sabotaged (e.g., database deletion)
- Site takeovers in their entirety
The fact is that there is no system that is entirely immune to APTs. As a result, it is on to enterprises and government agencies to ensure that compliance and security measures, like CMMC solution, are in place to suit the needs of their activities and the information they handle.
With that stated, there are a few things you can do to boost your odds of surviving an APT:
Rather than using blacklists, use whitelists: Any network that accepts connections might be a target for an attack… So, instead of building a blacklist for security, adopt a proactive approach to safeguarding critical systems by implementing a whitelist. A whitelist will prohibit all programs that aren’t allowed, closing several security gaps.
Maintain Modifications and Fixes: This might be difficult, but keeping your systems and technology up to date and protected against the current threats is critical. Old vulnerabilities might lay dormant for years before an attack pulls down your infrastructure. If you cannot manage patches and updates effectively, consider partnering with someone who can.
Enforce Strict IAM Authority: Identity and Access Management (IAM) is a critical security component and the point of entry for many hackers. IAM implemented incorrectly can allow a hacker to overcome otherwise robust biometrics or Multi-Factor Authentication and proliferate through critical systems with administrator restrictions.
Ensure Physical Security, Training, and Education: On-site security is equally as critical as networked security. Ensure that your personnel is properly trained in regulatory and security best procedures. Also, make sure that every workstation, data storage facility, or device is secured using compliance technology and common sense from your employees.
Maintain Compliance: While compliance isn’t a flawless technique, it may help you maintain a secure posture in the face of APT attacks. Additionally, One should not consider adherence and end objectives in isolation. Some frameworks, like CMMC compliance requirements, will incorporate particular standards for dealing with APTs, although not every industry will. Even if you are committed to complying, regularly ask what you should, can, and must do to ensure maximum security.
How APTs are a challenge for both large corporations and small businesses?
APTs are frequently thought of as massive assaults that target the most critical institutions, such as utilities, banks, military contractors, and federal agencies. However, as more organizations are dependent on data and cloud infrastructures to do business, APTs are becoming an issue for all firms.
To combat the growth in sophisticated assaults, we must all do our share to ensure good cybersecurity. That includes solid security engineering, control upgrades, patch management, ongoing monitoring, and intelligent compliance that targets real risks rather than ticking boxes. These measures will help you to protect personal information while securely conducting business.